
LATAEST ARTICLES
.png)
There are three main types of crypto wallets based on how users store their private keys. One type is a custodial wallet. Such wallets are easy to set up, simple, and convenient to use. They are usually offered by crypto exchanges to users for their convenience. Also, at the same time, while operating such wallets, you give up your financial freedom, because the private key is not in your hands. Wallet providers store private keys on their servers.

Another type of crypto wallet is a non-custodial wallet. On the one hand, they provide you with ultimate financial freedom. You may store assets, sell, and trade, etc. There are no restrictions or limitations set from the wallet provider’s side. On the other hand, the web3 environment is toxic and your crypto assets are the target for hackers and scammers. Also, the private key can be lost or misplaced, which will also disable access to the funds.
MPC technology is the gold standard in securing private keys
There is one more type of crypto wallet, a self-custodial. It provides you with full control over your digital assets and at the same time offers an unmatched level of security. Multi-party Computation (MPC) is the encryption technology that empowers you with convenient yet safe means to interact with web3.
What is MPC?
MPC is a technology that enables the data exchange between parties in a trustless manner and helps to build privacy-preserving software. The MPC technology protects your private key by splitting it into two (or more) shards.
Spatium stores one shard on your device (mobile phone) and the other one on the Spatium server.

When you want to sign a transaction and complete one of the actions: send crypto, buy crypto, exchange crypto, etc. a phantom key is generated. The wallet’s private key is eliminated, that’s why such wallets don’t have a single point of failure.
It’s worth mentioning that MPC is not easy to master. The technology represents multi-round distributed protocols with high-level cryptography. Inexperienced crypto development teams and lack of testing may cause MPC technology to be misused and prone to bugs. Moreover, in addition to signing crypto wallet transactions, MPC technology helps restore access to the wallet in case the device with the wallet installed is lost or stolen.
Spatium crypto wallet MPC implementation
Spatium Wallet has been applying MPC since 2017, which makes the Spatium team one of the most experienced in the world of MPC wallets. Also, as part of MPC technology, Spatium applies Threshold signatures (TSS) and Zero-knowledge proofs (Zk-proofs).
These technologies make consumer-focused Spatium wallets bulletproof secure and protect users’ on-chain asset management systems.
Only you, as a user, can initiate wallet operations. Spatium has no access to your wallet account. Also, Spatium cannot set any limitations on your wallet activity. To send crypto, you start a process when the wallet secret and the server secret communicate. Applied together, they sign a transaction without revealing the secrets to each other.
Summing up
Spatium Wallet is one of the first crypto wallets to use MPC. This technology is ideal for providing a balance between on-chain private key management, the ability to recover the wallet app and wallet security. Our team is advocating for a safe web3 experience available to everyone. Spatium Bitcoin MPC wallet is easy to use and free to download. It’s available on Android and iOS devices.
In addition to convenience, it brings a competitive edge by offering feeless transactions.
Try Spatium Feeless Bitcoin Wallet and the feature allowing you to pay network fee in currency you send instead of native chain tokens (currently available for USDC on Ethereum. More chains and tokens will be added soon).


%25201.svg)
Keep a close eye on Spatium Feeless Bitcoin wallet which is building DeFi on Bitcoin and actively working toward the introduction of feeless crypto transactions and cheapest ever peer-to-peer crypto swaps without escrow.
Follow us on social platforms: X, LinkedIn, Discord, and Telegram.
Backup in a crypto wallet is crucial. Web3 is different from web2 in terms of who takes the responsibility for asset protection and the safety of the wallet account. In web2 Fintech service providers are in charge, because the Internet of web2 is centralized. And even if you lose access to the app, the service provider will restore it to you easily and effortlessly.

The situation with web3 is the opposite because users are in charge of their crypto wallet account protection and safety. When you lose access to the wallet, you lose access to your digital assets forever. That’s why crypto wallet backup is important. It is an additional protection layer against emergencies: losing a mobile device with the wallet account, having it stolen or broken, etc. When the backup is on, you can restore access to your wallet anytime.
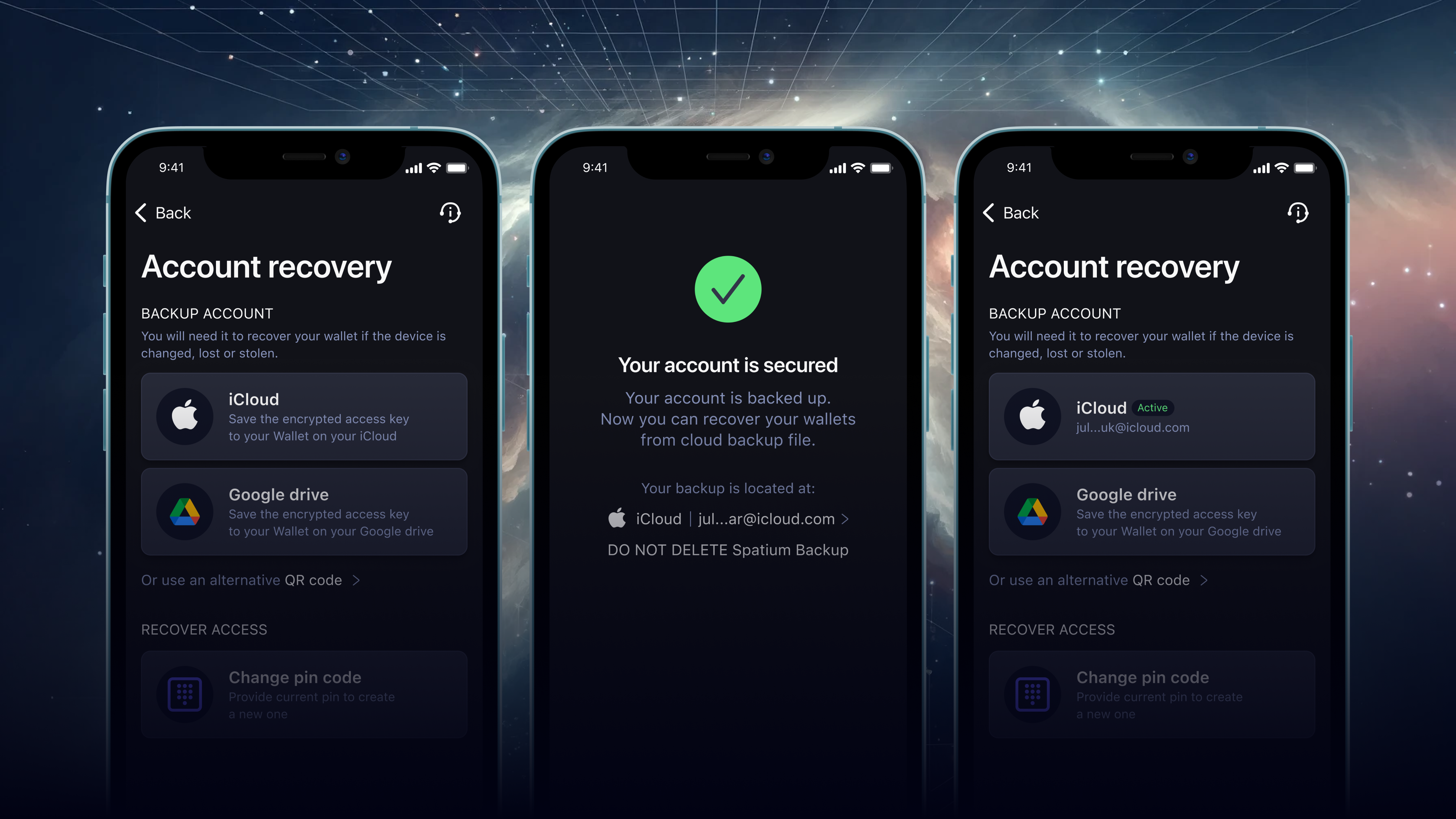
Let’s go through the Spatium cloud backup process and see how simple and quick it is.
How to set up Spatium wallet cloud backup?
Spatium Feeless Bitcoin wallet allows easy and convenient cloud backup using iCloud for Apple devices, Google Drive for Android devices, or a QR code. The cloud backup can be performed when you set up your wallet for the first time or added later after you start using the Spatium crypto wallet.
NOTE, in case you would like to use the Spatium wallet without the backup, bear in mind that the wallet functionality is limited. To get to know more about it, please, contact the Spatium team through the support form.
How to set up cloud backup if you register your Spatium wallet account for the first time?
If you don’t have a Spatium wallet on your mobile device you can set up cloud backup while setting up your wallet account.
- Go to the App Store or Play Market and download the Spatium Feeless Bitcoin wallet. It’s available on Android and iOS devices.
- Choose the preferred way to create your wallet account (Google, Apple, or email).
- Provide your consent concerning the fact that your cloud backup will be stored on your Apple iCloud or Google Drive. Please, make sure that you have enough storage on your Google Drive or iCloud. If you use an Apple device, make sure that your device has enough space for a cloud backup and the iCloud synchronization is on.
- Also, you have to give Spatium your consent on the fact that you understand that the ‘DO NOT DELETE’ file cannot be deleted. This file is located on your Google Drive or iCloud.
- One more important thing is that you provide Spatium with the consent that in case you ignore the previous warning and accidentally delete the ‘DO NOT DELETE’ file, then Spatium cannot help you restore access to your wallet account.
- Wait for the account registration and cloud backup to complete.
How to set up cloud backup if you already have a Spatium wallet account?
If you already have a Spatium account and would like to active a cloud backup then you should do the following:
- Go to the Profile, and click on Account Recovery.
- Check your cloud backup status.
- Choose the way to perform the cloud backup: Google Drive, iCloud, or create a QR code. NOTE, that Spatium recommends using more than one cloud backup option.
- Wait for your wallet account cloud backup to complete.
Setting up the Spatium backup with a QR code
If for some reason you don’t want to perform a wallet cloud backup through iCloud or Google Drive, you can always perform a wallet backup by creating a QR code. Also, even if you have already protected your wallet with iCloud or Google Drive backup you can still create a QR code that will act as an additional backup layer in case something happens to your Google Drive or/and iCloud.
- At any stage of cloud backup activation, you are provided with the option to generate a QR code.
- If you choose not to perform cloud backup through iCloud or Google Drive, you have to activate a QR code-based backup otherwise the functionality of your wallet will be limited.
- Please, note that storing a QR code in your gallery together with photos and screenshots IS NOT SAFE. We DO NOT RECOMMEND this. In case your phone is lost or stolen, you will lose access to your gallery which means that you will lose access to your wallet account.
- If you decide to perform your wallet account backup with a QR code, then it’s better to print it out and store it in a safe place.
- QR code is advised to be created in any case because if something happens to your iCloud or Google Drive, or you mistakenly delete the ‘DO NOT DELETE’ file, Spatium can still restore access to your account with the help of the QR code.
Conclusion
Backup recovery is a very convenient and important feature. Spatium Feeless Bitcoin wallet provides users with cloud backup performed through Google Drive, iCloud, or QR code. Spatium encourages you to perform more than one cloud backup. Use QR code generation as an alternative way to protect your phone in case you accidentally delete the ‘DO NOT DELETE’ file from your drives. Otherwise, Spatium won’t be able to help you restore access to your wallet account and funds stored there. Please, never delete the ‘DO NOT DELETE’ file.
Keep a close eye on Spatium Feeless Bitcoin wallet which is building DeFi on Bitcoin and actively working toward the introduction of feeless crypto transactions and peer-to-peer crypto swaps. Follow us on social platforms: X, LinkedIn, Discord, and Telegram.

One of the characteristics of web3 is transparency. Blockchain operations are viewed by all web3 members. While dealing with sensitive financial data one requires to be anonymous. But how can one perform transactions on the blockchain and stay anonymous at the same time?
The answer is quite simple - every single action on the blockchain is encrypted. Cryptography or encryption is the process of applying secret codes to encrypt financial operations and confirm the authenticity of crypto wallet owners.
Just to understand how important it is, check the latest report on scams and fraud in web3. There is no doubt that the figures will rise significantly if there is no encryption. And the participants of blockchain operations can be easily targeted.
Of course, not many of us can apply extremely difficult mathematical equations to make encryption work, we have it done for us. Anyway, understanding how crypto wallet’s public and private keys work is vital.

How are public and private keys generated?
In a combination: ‘private-public keys’ the heart of the pair is the private key. The public key is generated based on the private key, while both these keys are generated only once when you set up your crypto wallets for the first time.
Crypto wallet blockchain address (public address) looks like a long combination of random numbers and letters.
1Lbcfr7sAHTD9CgdQo3HTMTkV8LK4ZnX71Bitcoin0x1ABC7154748D1CE5144478CDEB574AE244B939B5Ethereum
Examples of public address for Bitcoin and Ethereum
It’s the first thing you see when you open your crypto wallet. Also, for convenience, these lines of randomly generated figures are displayed as QR codes. By scanning one of them, you are redirected to the crypto wallet.
In very simple terms public and private keys could be compared to emails and passwords. While you freely give your email address to anyone, you never share the password, right? Absolutely the same applies to crypto wallets: imagine that the email address is your public key and the password to your email is your private key.
While a public key is called a blockchain address of your crypto wallet and can be easily shared across the blockchain, your private key MUST be kept secret!
The private key is used to verify your transaction by signing it. Because the public key is generated based on the private key with the help of encryption, the blockchain has to verify that the pair is genuine. If the transaction passes verification, it’s confirmed and is written into the blockchain.
Keeping your private key safe
One more important thing you should know about the crypto wallet keys is that there is no reset button. Once the keys are generated they cannot be re-generated again in case they are lost or stolen. The seed phrase, aka your private key secret string of words, is unique and can be generated only once! This is why you have to be super careful and keep it safe.
Custodial Services
If you lose your private key, you have no access to your funds. That’s why there are multiple services online: crypto wallets and crypto exchanges. They store users’ private keys on their side and apply them if required. Such services are called custodial.
Pluses and Minuses of Custodial Services
On the one hand, private key custody is convenient, because you don’t have to wreck your head and stress out while operating a crypto wallet or trading at crypto exchanges. The interface of custodial wallets is straightforward, similar to a banking app or a digital wallet. You only have to press the button to send funds, buy, or sell. No extra manipulations are required.
On the other hand, no matter how secure your private keys are with the service they are still prone to hacker attacks or any other technical malfunctions. Once a custodial gets hacked and users’ private keys are stolen, you lose access to your assets forever. ‘Not your key, not your crypto’ they say and that’s exactly the case. Just to understand the scale of the problem, read about the largest cryptocurrency hacks.
Also, one more thing about centralized custodial crypto services is that knowing that they owe your private keys, they can introduce various regulations, in a similar way banks do. These could be account restrictions, increased withdrawal fees, etc.
Self-custody, where security meets convenience
Luckily there is another way to operate your crypto wallets - self-custody. Self-custody is a middle way that takes the best practices from custodial and non-custodial worlds and provides users with safe wallets, full ownership of their private key, and convenience of operation. Keep tuned to our news and we will discuss more of what self-custody is and what’s the role of Secured Multi-Party Computation (MPC) in it.
Spatium crypto wallet which is self-custodial is free for everyone. We make sure that your digital assets are securely protected and that there is no friction while using our wallet app. Download, try it, and enjoy making financial decisions independently, irrespective of banks and other financial institutions.
Self-Custodial & Feeless Wallet from Spatium
Spatium Wallet is a multi-currency wallet that works with Bitcoin blockchain as well. Our wallet is making crypto swaps available to everyone through lowering commissions due to the feeless feature, and minimizing the number of intermediaries. Check out wallet website for more information and stay tuned!
Try Spatium Feeless Bitcoin Wallet and the feature allowing you to pay network fee in currency you send instead of native chain tokens (currently available for USDC on Ethereum. More chains and tokens will be added soon).


%25201.svg)

To use and trade cryptocurrencies you need a crypto wallet. It’s a special software that allows you to check your balance, send or receive crypto. At first glance, crypto wallets look similar to traditional banking or payment apps. But they work in a completely different way.
We would like to discuss several important points in this guide:
- Why do people use crypto wallets?
- How do crypto wallets work?
- What are public and private keys?

Why Do You Need a Crypto Wallet?
Right now, a crypto wallet is the only means to interact with blockchain networks. Similar to the way banking apps don’t store any of your money (banks do), crypto wallets also don’t store any of your digital assets. By digital assets, we mean cryptocurrencies or tokens.
For example, if you have 10 Bitcoins and you would like to send 1 Bitcoin to your friend or relative, you do this within the wallet, but in reality, you transfer the ownership over this digital asset to the other person. So there is no third party involved.
Crypto wallets exist in various forms and shapes. Some of them come as an app on the phone, some act as a program on your computer or a service where you can log in and get access to the web3.
How Do Crypto Wallets Work?
To get an understanding of how crypto wallets operate, we have to talk about cryptography and encryption techniques. Imagine what might happen if, in a zero-trust environment, which is web3, anyone can access your private information regarding transactions. For some ill-minded people with technically advanced skills, it’s a red flag in front of a furious ox. They will try to hack your wallet and steal your funds.
That’s why all activities on the blockchain are encrypted by default, including crypto wallet operations, private and public keys. Encryption in simple words is a secret code used to protect users’ communications and information.
Web3 is almost a war zone, as it applies high-level cryptography, or encryption similar to one used in the military. It is based on advanced mathematical equations, and it’s quite common that a crypto wallet uses more than one encryption technique. Cryptography is used to sign, send, and receive transactions.
Basic Crypto Wallet Activities:
- Showing your crypto balance
- It means that your crypto wallet has access to any computer around the globe that stores a blockchain with your assets. Luckily for you, web3 doesn’t have a single point of failure and as long as there is at least one working computer with the blockchain database stored on it, you will have access to your digital assets.
- Building a transaction
- Before making a transaction you have to construct it and provide all the essential parameters. These are the amount of funds to be sent and the destination (another person's wallet or your wallet on a different blockchain).
- Signing a transaction
- This is the step when your crypto wallet starts actively using encryption. A transaction requires a cryptographic signature to safely send it to the blockchain.
- Sending a transaction to the blockchain
- This is the stage when a crypto wallet finally sends a transaction to validators. These are special people, miners who are responsible for the verification of all transactions sent to the blockchain and updating the ledger (blockchain) balance.
Public Keys and Private Keys
For a crypto wallet to operate on blockchain it requires private and public keys.
Public key
The public key is your wallet’s blockchain address. It’s generated once when you set up your wallet and is given to anyone who wants to send you assets. Also, you have to know other people's blockchain addresses (public keys) to perform a transaction and send funds to their wallets.
Private key
The private key is generated together with the public key when you set up your wallet for the first time. But unlike the public key which is shared right and left, your private key cannot be shared with anyone!!! You have to keep it private and sign with it only trustworthy transactions.
Usually, a crypto wallet's private key is represented by random words (from min 12 to max 24), a seed phrase. At the same time, there are new types of wallets taking web3 by storm - MPC wallets and smart contact wallets that don’t require a seed phrase to operate.
Conclusion
There are several strong arguments for using crypto wallets and storing cryptocurrency there. One of them is that blockchain doesn’t have a single point of failure and in any emergency case you will still have your assets and get access to them.
One of the most convenient and safe crypto wallets is Spatium. Spatium crypto wallet app is available on iOS and Android.
Download it and and try Spatium Feeless Bitcoin Wallet and the feature allowing you to pay network fee in currency you send instead of native chain tokens (currently available for USDC on Ethereum. More chains and tokens will be added soon).


%25201.svg)

Bitcoin price is on the rise and web3 users might be inquiring what is the way to get Bitcoin, how it works, and why it’s a good idea to get one. Bitcoin is the first digital currency that is completely decentralized, anonymously owned, and transferred. It is out of reach for banks, governments, or any other financial or centralized institutions. Let’s discover more about it.

History of Bitcoin
Bitcoin came into existence in 2008 with the creation of the Bitcoin blockchain by Satoshi Nakamoto. He discovered a way to create a financial network where anonymous peer-to-peer transactions became a reality. In other words, the Bitcoin blockchain is a public ledger that holds the records of all transactions since the first hour of its existence. As long as the Bitcoin blockchain exists at least on one of the setup servers (nodes) anywhere around the world, the whole network is working.
How Does Bitcoin Blockchain Work?
The decision on who is the owner of a Bitcoin coin is made cryptographically across the nodes running the blockchain. No central entities are required. Anyone who provides a dedicated server placed on their computer, aka node, can participate in the transaction verification process. Bitcoin transactions are transparent and transferred from one node to another.
All Bitcoin transactions are written in blocks and stored online. Each block takes 10 minutes to form. When the block goes online, all transactions written there become visible to everyone. These blocks can not be removed or rewritten, they stay in the blockchain permanently.
If we talk about money transfers, let’s discuss what happens when User1 transfers 1 Bitcoin to User2.
First of all, User1 and User2 should have a crypto wallet to see their balance and initiate the transaction.
Secondly, it’s important to understand that crypto wallets don’t hold assets, the Bitcoin blockchain does.
Thirdly, if User1 sends 1 Bitcoin to User2, they just rewrite the ownership, in other words, add a new ownership to the digital asset. The change of ownership is written into the block and placed online. After the block goes live, the crypto wallets of User1 and User2 reflect new writings. The account of User1 has minus 1 Bitcoin and the account of User2 has plus 1 Bitcoin.
Sharing Bitcoin is possible due to the agreement among the network nodes about the ownership of a Bitcoin. A crypto wallet is used as an interface. It helps users to initiate a transaction and reflect the account status.
Why Will the Bitcoin Price be Extremely High in the Future?
Right now Bitcoin price is quite expensive. Starting from $0 for a coin in 2009 it rose to $50,000 at the beginning of 2024. The fact that Bitcoin's total amount is limited by design, will make it eventually an endangered species. The question is when it will go extinct: in 5 years, 10 or 30? As soon as there are no more new Bitcoins, a big fight for the market will start and Bitcoin price will skyrocket.
Summing Up
Bitcoin is the first and the most protected blockchain in the web3 ecosystem. It’s decentralized and anonymous. Due to such characteristics, Bitcoin remains the most expensive cryptocurrency and the most wanted one.
Spatium Wallet is a multi-currency wallet that works with Bitcoin blockchain as well. Our wallet is making crypto swaps available to everyone through lowering commissions due to the feeless feature, and minimizing the number of intermediaries. Check out wallet website for more information and stay tuned!
Try Spatium Feeless Bitcoin Wallet and the feature allowing you to pay network fee in currency you send instead of native chain tokens (currently available for USDC on Ethereum. More chains and tokens will be added soon).


%25201.svg)

Web3 is a decentralized version of the internet gaining popularity worldwide. It brings new opportunities for communication, business and entertainment. Blockchain introduces a new brand of economic system, a new generation of games and social media. Web3 development is growing rapidly. For example, the number of active blockchain wallets has increased by 639%, and there has been a significant growth in the number of active GamFi users.

However, Web3 technology still remains IT-based, which means it has its own vulnerabilities that need to be addressed. It is essential to understand and address these vulnerabilities to provide the security of Web3 solutions.
Read this article and find out about the top 10 Web3 vulnerabilities, their challenges, and solutions to help businesses protect themselves from potential attacks.
Fundamentals of Web3 ecosystem
Let’s start from the beginning. Web3 refers to the next generation of the internet that is decentralized, making it totally different from Web2. In Web3, the client-server model is replaced by a distributed one. It’s main principles are:
Decentralization. The whole global system’s not controlled by a single company. Instead, it consists of a network of nodes working together. In this way, they maintain the integrity, efficiency and security of Web3.
Blockchain technology at the core. This is a distributed database shared among a computer network's nodes. Blockchain ensures security and transparency while storing and transferring data.
Smart Contracts.They are self-executing contracts with embedded terms of the agreement between two addresses. This kind of agreement’s directly written into the code. Smart contracts automate transactions and reduce the services of interceders.
Web3 is designed to be interoperable. It means that it can work with other networks and protocols. Developers can build a crypto project that directly interacts with other applications and even networks.
Finally, Web3 users can create non-fungible tokens, which can represent assets and currencies.
These fundamentals of Web3 are boosting the adoption of decentralized solutions and improving the way businesses operate with customers.

The Benefits of Web3 Platforms for Businesses
In the B2B sector, Web3 is improving the way businesses operate. Moreover, for Web3 builders, product managers, and C-level executives, the adoption of Web3 technologies can be a new opportunity to scale their capacities.
Enhancing User Experiences
Web3 technologies let create decentralized applications that offer user-centric experiences. Users can now have full control over their data, identities, and digital assets.
Automation
Smart contracts automate and streamline complex business processes and reduce costs. For example, supply chain management can be improved by using smart contracts. They track and verify the authenticity of products, their logistics etc.
Collaboration
Web3 increases interoperability among platforms and ecosystems. Through blockchain protocols, businesses securely connect and share data, thereby leveling up the efficiency of the connection.
Global Reach and Accessibility
Through peer-to-peer transactions, borderless payments with cryptocurrencies and accessibility for the unbanked, the technology helps reaching customers worldwide. There’s no more traditional banking systems and international money regulations.
In general words, the benefits of Web3 for businesses are exceptional. They help create secure websites and transactions, new revenue streams and build lasting relationships.
How Businesses Are Using Web3 Infrastructure
Below you’ll find top 5 use cases of the technology’s adoption:
- Decentralized Finance (DeFi). Such kinds of protocols offer financial services without the commissions and approvals. For example, users of the DeFi crypto wallet can trade assets directly with one another, without the participation of traditional banks in this chain.
- Non-Fungible Tokens (NFTs). With it, businesses tokenize and sell digital assets, They might be real estate, commodities, water etc. For the artists, musicians, and content creators NFT marketplaces are a perfect way to sell the digitized creations to fans.
- Supply Chain Management.With blockchain, smart contracts, and IoT devices, companies extend the life cycle of a product.
- Decentralized Governance. Web3 allows creating Decentralized Autonomous Organisations and uses specific tokens for the decision-making. Businesses can utilize these tokens to let their users vote and take part in the project’s life, increasing their engagement.
- Tokenized web3 community rewards. New technology helps businesses create tokenized rewards to reward user engagement and loyalty. As an example, a blockchain-based social media platform could be built that encourages users with cryptocurrency for creating and curating content.
As you see, businesses can enhance trust, security, and transparency in their interactions. Also, they’re exploring new ways for value creation and revenue generation.

Top 10 Security Risks in Web3
Web3 might look like an invincible creature. However, as with any IT-based product, it’s susceptible to software bugs, security issues, and other vulnerabilities. They may represent traditional risks to businesses that may lead to the economic impact, data breaches, and reputational damage. Malicious actors can exploit these vulnerabilities to compromise websites, leak data, infect databases, and conduct injection attacks.
Moreover, the nature of Web3, with its reliance on network consensus and decentralized architecture, introduces new security challenges. It makes it important for businesses to understand and address these vulnerabilities to protect dApps and users’ assets.
So, the weak points are:
- Smart contracts are inclined to coding errors and reentrancy attacks or unchecked external calls.
- Blockchain Consensus Attacks. This means the attempt to disrupt the agreement process among participants. For example, in a network with proof-of-work (PoW) consensus mechanism, a 51% attack happens when an individual or group obtains control of more than 50% of the network's mining power.
- Decentralized Applications (DApps) may suffer from insecure permissions, or inadequate access controls.
- Web3 wallet can be an easy target for attacks like phishing, keyloggers, or malware.
- Oracles, which connect smart contracts with external data sources, can introduce problems if data sources are unreliable. In this case, such a dysfunction can lead to manipulated data being embedded into the smart contracts.
- Cross-site scripting vulnerabilities can enable attackers to inject malicious code into dApps. It will threaten user data at least.
- DoS Attacks can disrupt Web3 services. They overwhelm networks with excessive traffic or resource consumption.
- Users could be victims of the phishing attack and social engineering tactics, where attackers deceive users into revealing sensitive information or accessing malicious websites.
- Injection attacks API security vulnerabilities and it may lead to the loss of funds, disruption of service etc.
- Identity and Access Management Issues. Insufficient quality of the KYC and authentication process could lead to identity theft.
Understanding these potential issues is important for building secure and resilient businesses in the Web sphere.
Challenges in Addressing Web3 Vulnerability Cases
Except for the precise vulnerabilities, the essence of Web3 may be concidered as an obstacle while establishing centralized security measures. It operates on a distributed network, making it difficult to implement comprehensive protective measures across all nodes.
Moreover, the complexity of smart contracts poses a challenge. Written in code, they are vulnerable to Web3 bugs and loopholes that may go unnoticed until triggered.
Another challenge lies in the lack of regulation within the Web3 ecosystem. As it continues to evolve, there are not enough accepted frameworks. This creates an environment where security practices and protocols vary. They may cause inconveniences during the establishing interconnections and may bring significant expenses.
Furthermore, Web3 technology introduces new attack vectors that were not present in previous iterations. Novel exploits emerge as new protocols, web3 libraries, platforms, and applications are developed.
So, addressing Web3 vulnerabilities is a complex task that generally requires strong security measures and collaboration.
Top 5 Significant Web3 Hacking Events
Unfortunately, the industry has significantly suffered from the imperfection.
Wormhole Bridge Hack
In February 2022, the Wormhole bridge, a cross-chain communication protocol, was exploited to steal $326 million in cryptocurrency. The attackers manipulated the bridge's vulnerable code to mint a large number of tokens and then exchanged them for other cryptocurrencies.
Beanstalk Farms Hack
An individual utilized web3 hacking tools against the DeFi protocol Beanstalk Farms and stole $182 million. They used a flash loan attack to manipulate the protocol's pricing mechanism and then run off with a large amount of its native token.
Nomad Bridge Hack
The Nomad bridge, another cross-chain communication protocol, has lost $190 million. The attackers used a similar technique to the Wormhole hack. Then they minted a large number of tokens and then exchanged them for crypto.
Mango Markets Exploit
The decentralized exchange Mango Markets has suffered losses by $114 million. The criminals used a combination of techniques to drain the DEX's liquidity pool.
Rari Capital Exploit
The DeFi protocol Rari Capital was exploited to steal $150 million. The perpetrators employed a comparable method to the Beanstalk hack, exploiting the protocol's pricing mechanism to get its native token.
As the Web3 ecosystem continues to grow, it is likely that we will see even more damaging attacks. It is therefore essential for developers and users to take steps to create efficient systems that protect themselves from these threats.

Web3 Cyber Security Solutions
So, what should a business do to avoid becoming a victim of hackers? Reducing Web3 vulnerabilities requires an approach that involves integrating security governance, analysis, and following security-by-design principles.
Here are some additional solutions to fix Web3 vulnerabilities:
- Conduct assessments and audits of smart contracts, protocols, and decentralized applications. They are needed to identify weak points early in the development process.
- Implement best practices for securing smart contracts. Use formal verification tools, testing for edge cases, and avoiding a remote control vulnerability. This is applicable for the cloud solutions too, see the Spatium Wallet Cloud case.
- Use secure coding practices, such as input validation, output encoding, and error handling.
- Minimize attack surface areas, secure defaults, and implement zero-trust framework.
- Establish secure defaults through a selection of systems with secure settings. Prepare strong passwords, and remove unwanted features.
- Use multi-factor authentication and encryption to protect user data and crypto coins as Spatium SDK does.
- Regularly update software to patch vulnerabilities and address threats.
- Build a strong and resistant UI-interface. You can start from scratch or use already existing solutions such as Spatium Wallet UI Kit.
- Provide a reccuring dapp security guidance for developers.
- Conduct web3 bug bounty programs. The community readily engages in such initiatives.
By implementing these solutions and best practices, businesses can prevent the Web3 security breach and protect their products and users.
Final thoughts about web3 security
The evolution of Web3 technologies brings both benefits and challenges. Ice phishing, cryptojacking, smart contract logic hacks, and data manipulation in dApps, underscore the need for innovative security measures within the Web3 ecosystem.
There are already best practices that should be implemented to avoid unpleasant consequences. Secure coding, regular code audits, and ongoing security monitoring can help reduce vulnerabilities.
As Web3 companies move forward, it’s important for developers, auditors, and users to remain vigilant, stay informed about threats, and implement robust security measures to safeguard the integrity and functionality of Web3 applications. This stance towards Web3 security will be contributory in nurturing trust, boosting innovation, and realizing the full potential of blockchain.
FAQ
Is Web3 vulnerable?
It looks like Web3 is still vulnerable and represents some specific Web3 limitations. The total losses in DeFi are over $7 billion in 2023. This is still a high number in the Web3 market. Even though lately figures have decreased, hacks of a different kind and scale happen regularly. But the security systems continue to evolve, blocking paths for attackers.
What is a unique security challenge in the Web3 space?
Decentralization means there is no single point of control, which naturally creates a significant security challenge. A Web3 platform is made up of multiple nodes, and each node could potentially be a point of vulnerability if not adequately secured. This increases the attack in Web3 dramatically.
Why is wallet security important in Web3?
Web3 users require digital wallets to store and manage cryptocurrencies. However, wallets are exposed to phishing, rug pulls, malware, and social engineering. Therefore, users must practice strong security measures, including enabling two-factor authentication. On the other hand, developers should practice secure coding, regular audits, timely updates, and continuous monitoring.
What are Layer 3 security threats?
Layer 3 protocol attacks consist of Internet Protocol, packet sniffing and DoS attacks i.e. ICMP attacks or ping of death. These types of attacks can be performed remotely. To reduce the risk of these types of attacks, packet filtering controls should be used.







